The Basics of Cyber Safety Computer and Mobile Device Safety Made Easy
In principle, mobile security has all the same goals as desktop security, but the implementation and preventative measures that IT must put in place are often quite different.
Organizations need to lock down all devices that access business data, and put measures in place to ensure that their data won't fall into the wrong hands. This general goal applies to all types of enterprise security -- network, PC, laptop, application -- but mobile security offers unique challenges for organizations to grapple with.
For example, device loss and theft are far more of a security concern for mobile devices than other types of endpoints. Mobile devices can also operate without traditional Wi-Fi or Ethernet connections and in any location that has a decent wireless signal.
Organizations should turn to mobile-specific tools, products and policies that can enable workers to be productive on their mobile devices while ensuring the security of the device and its data.
What role do mobile devices have in business?
The modern workforce is more mobile than ever due to numerous factors, including the proliferation of laptops, hybrid devices, tablets, smartphones and other mobile devices. These devices allow workers to be productive from a variety of locations, such as at home, at an airport or in transit.
Working remotely and while on the go is a well-established concept in the enterprise and in organizations of all sizes. Mobile devices such as smartphones and tablets have a major part to play in enabling workers to do this. For example, many workers carry around smartphones with access to work email and business applications everywhere they go.
But, mobile devices can enable more than just on-the-go work. Tablets and smartphones can be used for point of sale (POS), record-keeping, data logging and custom form submissions. Mobile devices can even serve as full workstations with the proper auxiliary device support.
When it comes to securing mobile devices, personal devices have far more security concerns and complications compared to single-use kiosk approaches. The attack surfaces for kiosk devices are far smaller than those of employees' personal smartphones due to the wider array of applications and freedom to browse the Internet. As such, mobile security policies should focus predominantly, but not exclusively, on securing these types of devices.
Another common type of mobile device in the enterprise is a corporate-owned mobile device. Some organizations have the capital to purchase mobile devices for certain employees. Securing these devices is relatively straightforward -- especially compared to personally owned devices accessing corporate data -- and IT admins can apply strict security controls to these devices.
What are the benefits of mobile devices in the workplace?
The most obvious benefit of mobile devices is the flexibility they provide for employees to be productive from various locations. Laptops were the first step in the evolution toward enabling mobility with business endpoints, and mobile devices such as smartphones were the next step. In general, mobile devices enhance connectivity, communications, collaboration and networking due to their portability and access to cellular networks. The accessibility of an organization's resources improves dramatically with mobile devices in the mix.
Users can access business email, unified communications (UC) mobile apps such as Microsoft Teams and Slack, custom business applications and other apps or services that enable productivity. This benefits knowledge workers and executives especially, as they may need to respond to critical emails or approve certain workflows while on the go or from remote locations.
End-user smartphones aren't the only major use case for mobile devices within an organization. Kiosk devices that serve a single purpose are a key part of numerous types of organizations. Tablets, smartphones and other mobile devices can assist with POS needs, customer or client registration, digital waiver signage, data input and much more.
Why do businesses need a mobile security policy?
It may be easy to overlook mobile devices in a security policy; after all, they are rarely a user's main workstation. This is especially the case when it comes to users connecting their personal devices to work applications and services, such as an organization's email server or UC platform.
However, organizations that allow for any access to work data on mobile devices absolutely must have some sort of mobile security policy. It may be helpful to think of it as the "weakest link in the chain" principle: Company data is only as secure as the least secure device accessing it.
Neglecting mobile device and data security leaves striking vulnerabilities in an organization's overall security architecture and policy. Therefore, a security architecture that includes mobile-specific policies such as acceptable use guidelines for mobile device users, mobile security best practices, and security platforms or services is essential for organizations that rely on mobile devices.
Choosing a mobile device policy: Corporate owned vs. BYOD
One of the first steps in establishing a mobile policy is determining whether users' devices will be corporate owned or user owned. Each approach has its strengths and weaknesses that organizations have to factor in. Generally, corporate-owned devices provide more certainty and simplicity from a management and security policy perspective, but BYOD allows for more user choice and flexibility.
Considering corporate-owned mobile devices
Issuing corporate-owned mobile devices to users is the more straightforward and expensive option for organizations. The biggest benefits of a corporate-owned approach are IT's security and management capabilities. Organizations can maintain as restrictive of a device policy as they want without having to worry about invading users' privacy on their personal devices. Users are more likely to be understanding when it comes to a device that they didn't purchase themselves. The process of deploying app and OS updates is also easier with full device control because users typically prefer to update their personal devices on their own schedule.
A company-owned device program isn't perfect for every situation. For example, organizations that assign mobile devices to users have to pay for those devices. Organizations can negotiate deals with smartphone manufacturers -- but even with discounts, the cost of all that hardware can add up quickly. Larger organizations may not have this issue when it comes to resources for mobile device purchases, but small or tight-budgeting organizations may not want to incur this cost.
Additionally, organizations must decide if corporate-issued devices are allowed to serve as users' personal devices as well. Users may appreciate the lenience of having a corporate-owned, personally enabled (COPE) device for the flexibility. However, plenty of users have their own smartphone or other mobile devices before joining an organization, so this may not be necessary. The corporate-owned, business-only (COBO) approach allows organizations a very high level of control over the device, its security and privacy policies, its update schedule and much more.
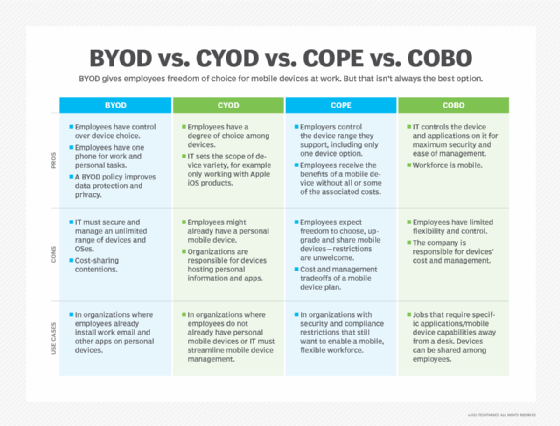
Looking into BYOD
Many organizations may see BYOD as the simplest and most straightforward device deployment option. The organization doesn't have to purchase new mobile devices for each new hire, and users can have a single device for both work and personal matters. Carrying around multiple mobile devices could lead to a poor user experience and employee frustration. The BYOD approach is straightforward, but it can prompt more complicated security policies and management compared with COPE and COBO.
For example, users have to agree to the organization's terms of device use and mobile policy before they start using their personal devices for business tasks. This could include forced OS or app updates for security, on-device management agents and an overall decrease in the users' privacy. There is also the issue of cost sharing. Some users -- especially those who work with their mobile devices quite a bit -- incur additional costs such as data use, device repairs or even device replacement. If organizations can shape a policy to account for these BYOD factors, then BYOD could be an ideal option.
Comparing BYOD vs. corporate-owned security
In very general terms, corporate-owned devices provide stronger security for organizations. This is due to the IT administrator's ability to control devices more closely compared to BYOD deployments. A BYOD security policy needs to account for users accepting the level of device control that an organization asks for. As such, organizations are more likely to offer more lenient security policies to ensure user acceptance.
Corporate-owned devices don't have this level of ambiguity when it comes to user acceptance. For example, IT admins can deploy a policy that allows for remote device wipes without worrying about deleting a user's personal device data.
IT administrators should note that a mobile policy's level of security is determined based on the controls IT implements and not the device ownership model. But the path to a strong mobile security policy is simpler for corporate-owned devices.
What are the risks and challenges of mobile device security?
The benefits of mobile devices are widespread and can fit within a huge amount of use cases. However, mobile devices bring more attack surfaces and other challenges that IT and end users need to address.
While there is a perception that mobile devices aren't susceptible to threats, this is categorically not the case. Like any endpoint, hackers can intercept ingoing and outgoing traffic from the device, trick users into downloading malware and access users' data via a compromised network connection.
Further, mobile devices face additional threats that typical endpoints do not. Device loss and theft are more common with mobile devices, and social engineering attacks are extremely common with the numerous vectors that mobile devices allow. Phishing attacks that target certain employees' mobile devices can use SMS messaging, email accounts, messages via numerous social media applications or even malicious links in browsers.
There also may be challenges with integrating mobile devices into existing back-end systems, legacy and custom applications, and services that are tailored to endpoints such as PCs and laptops. It's great to provide users with access to email and basic corporate services, but the cost of deploying and managing these mobile devices may not be worth it for certain organizations if they can't access all company systems. Most business technology vendors are aware of the role of mobile devices and provide products and services that accommodate mobile devices, but mobile support isn't universal. This is especially true with custom and legacy applications.
These compatibility problems can morph into larger issues of compliance as well. Highly regulated fields, such as government, finance and healthcare, may have difficulty enabling mobility while abiding by each sector's regulatory laws.
Steps to define and implement a mobile security policy
Organizations can mitigate the security risks and shortcomings of mobile devices with a specific and effective mobile device policy. This is especially true with the mobile security components of that policy.
Mobile policies should be detailed, comprehensive and largely customized based on an organization's needs. While it can be helpful to start a mobility policy from a template, organizations have to define certain components, including acceptable device use, device ownership policy, privacy policy and disclosure of what data the organization can view. The policy should also explain what on-device security and management agents will be present, and what measures an organization can take to ensure data security -- e.g., can an organization run a remote device wipe if it is compromised or remotely lock the device if it is at risk.
Once IT staff and management collaborate to build the mobile security policy, there is still work to do. Organizations must find the best way to outline this policy and communicate it to end users; a policy is only effective if users understand and adhere to it. Ideally, users should review the documentation during the onboarding process.

Organizations should track who needs to review the mobile policy and verify that each user accessing business data with a mobile device has read the necessary documents and completed any security awareness training.
Additional mobile security best practices and measures to consider
Mobile devices are more susceptible to theft than laptops and PCs, so ensuring that mobile devices have robust authentication requirements is essential. Organizations can require stronger mobile authentication strategies, such as an eight-character minimum for device passwords instead of numeral-only PINs, or even two-factor authentication. The two-factor approach could supplement a passcode with additional measures, such as biometric factors -- usually a fingerprint or iris scan -- a user location verification or a secondary authentication device such as an ID card or chip.

Direct device theft is far from the only way hackers target mobile devices. Cybercriminals often target mobile devices over public Wi-Fi networks. Because these networks don't require any authentication, hackers can prey on unsecured devices that are connected to that network. Further, some hackers set up their own public Wi-Fi networks that imitate free Internet from businesses such as coffee shops or restaurants. Organizations should restrict access to unsecured public Wi-Fi via a management console if possible and, at minimum, explain these dangers in the mobile security training and documentation.
These best practices can make up a strong mobile security policy, but IT administrators also need to think about how they can enforce these controls. The most ubiquitous approach to mobile policy enforcement is mobile device management (MDM) platforms. Vendors often bundle these management platforms into larger offerings, such as enterprise mobility management (EMM) and unified endpoint management (UEM). The larger offerings include broader management capabilities; for example, EMM includes mobile application management (MAM) capabilities alongside MDM controls. UEM takes all that EMM offers and expands it to all types of endpoints, including laptops and PCs.
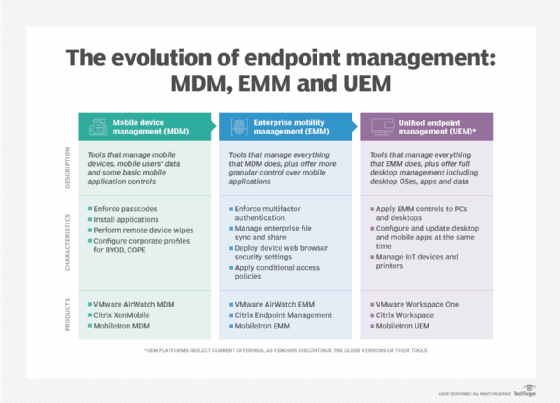
Most EMM and UEM platforms include both MDM and MAM capabilities. Organizations may also want to consider mobile threat defense (MTD) platforms, which offer more advanced security management capabilities than MDM or MAM. For example, some MTD platforms offer phishing and spam filters, device health reports, malware scans and behavior analysis.
IT administrators must find an MDM platform and other supporting technologies that can meet their device security and management needs. It's impossible to walk through all the potential integrations, features, licensing models and support that different organizations could need, so IT administrators should work with executives and perform diligent market research before selecting the ideal product. This could include working with product demos, talking directly to vendors, and consulting with independent researchers that evaluate mobile security and management offerings.
Source: https://www.techtarget.com/searchmobilecomputing/The-ultimate-guide-to-mobile-device-security-in-the-workplace
0 Response to "The Basics of Cyber Safety Computer and Mobile Device Safety Made Easy"
إرسال تعليق